Hipaa Policies And Procedures Manual Template. General Rule A Covered Entity may not use or disclose PHI except as permitted or required by the privacy regulations. With a Consent, to carry out treatment, payment, or health-care operations.

Human Resources Policies & Procedures Manual - Xavier University.
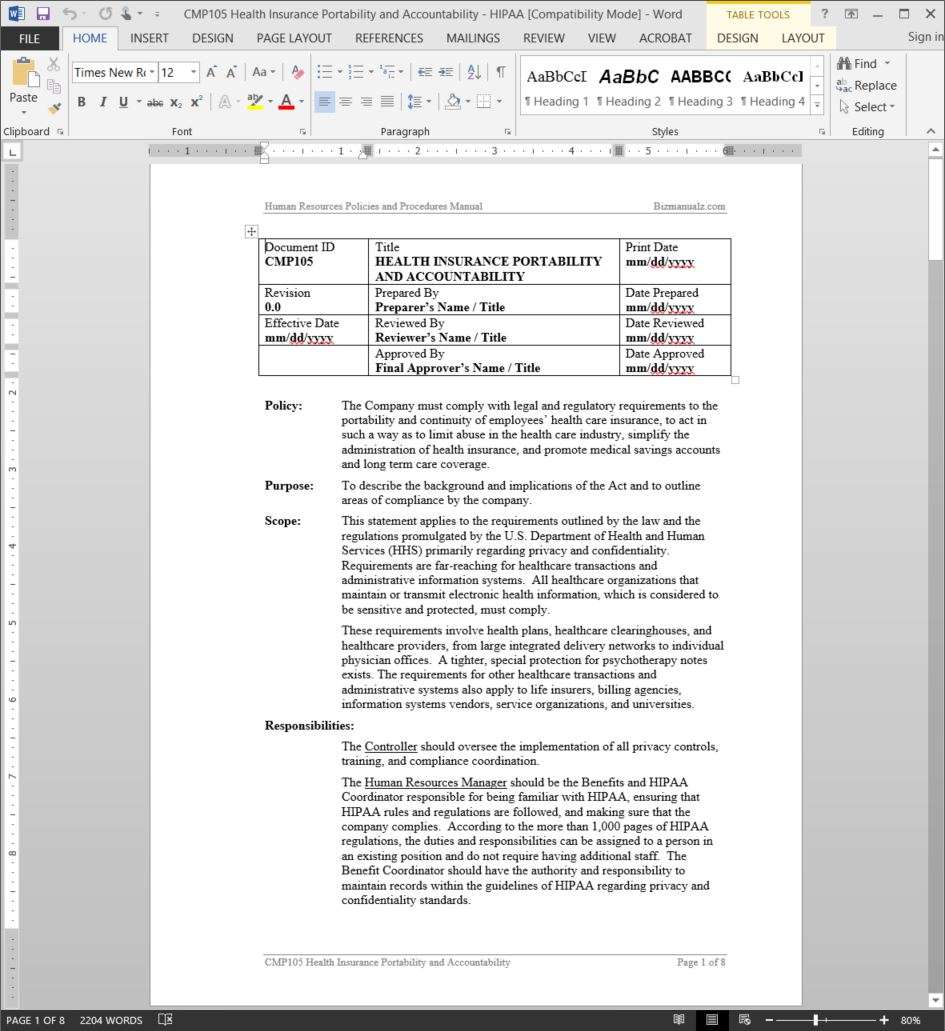
These documents are a model HIPAA Policy and Procedure Manual, published by the Long Term Care Consortium (LTCC).
Policy and Procedure Manual Compliance Management Made Easy -- Califorina Consumer The Security Manual has recommended policies, procedures and written agreements with employees Job Descriptions for the Chief Secrutiy Officer and Chief Compliance Officer. HIPAA Standard: Implement policies and procedures for authorizing access to electronic protected health information that are consistent with the applicable requirements for subpart E of this part. Implement policies and procedures to protect health information from improper alteration or Implement policies and procedures to prevent, detect, contain, and correct security violations.