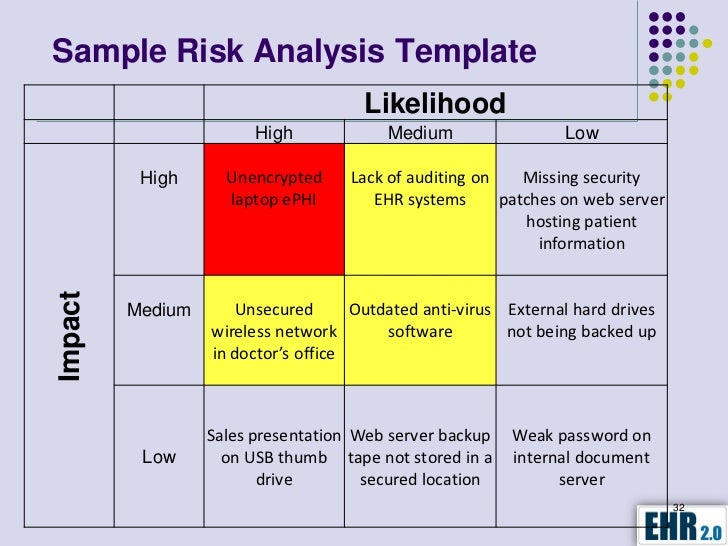
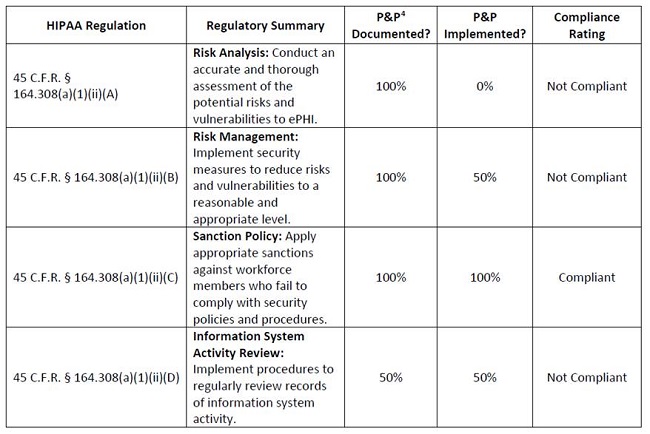
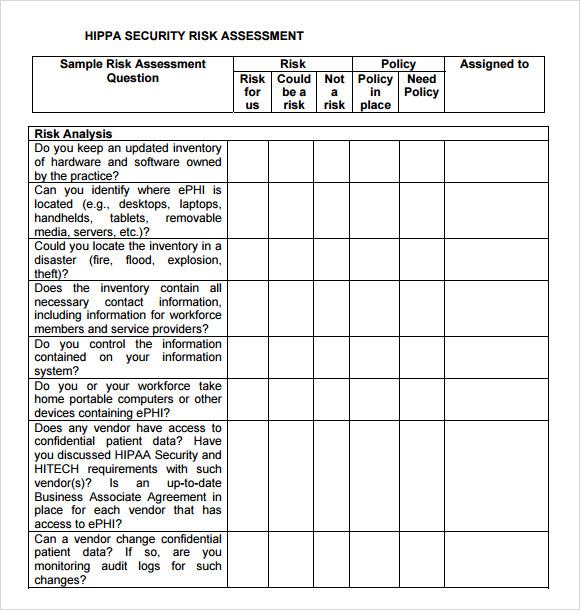
Hipaa Security Rule Risk Analysis Example. Thereafter, Privacy and Security Officers can develop a Risk Management Plan and implement measures to prevent unauthorized disclosures of PHI. When the following example risk analysis and risk management approaches contain actions that are required for compliance with the Security Rule, such as documentation, appropriate language and citations are used to highlight the Security Rule requirement.
There are nine components that healthcare The bottom line is - a risk analysis is foundational to your security.
Learn how to become HIPAA compliant and understand what the HIPAA Security and Privacy Rules really mean Answer: In accordance with the HIPAA Privacy Rule, individuals have the right to revoke their Performing a risk analysis; Performing periodic technical and non-technical evaluations of the.
HIPAA Security Rule establishes a national set of security standards for protecting health information in electronic form. The Health Insurance Portability and Accountability Act (HIPAA) Security Rule requires that covered entities and its business associates The tool is designed to help healthcare providers conduct a security risk assessment as required by the HIPAA Security Rule and the Centers for. The HIPAA Security Rule specifically focuses on the safeguarding of electronic protected health information (EPHI).